Understanding Network Protocols: OSI Model, TCP/IP, and UDP
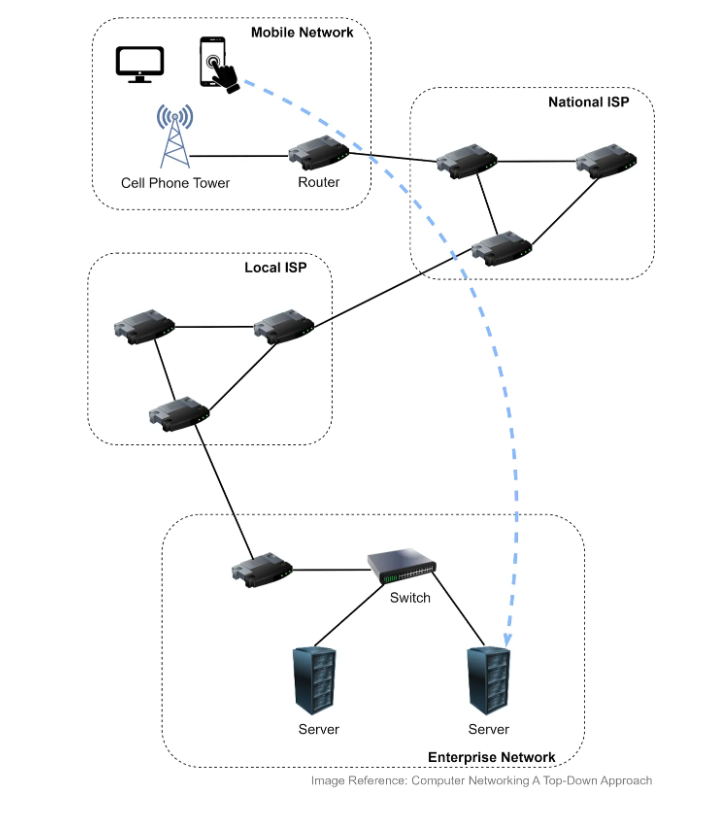
In today’s interconnected world, the Internet serves as a bridge linking countless computing devices across the globe. Whether you’re accessing a website from your smartphone or conducting a video call on your laptop, the data that enables these activities travels through a complex network of devices and protocols. Imagine accessing a website from your device: your request is first transmitted to a nearby cellular tower or router, which then forwards it through various Internet Service Providers (ISPs). These ISPs route your data through the internet, eventually reaching the network hosting the website. Once there, the data passes through a series of switches and routers until it reaches the intended server.
At the heart of this process are network protocols, the rules that govern how data is transmitted, routed, and received. Routers and link-layer switches play crucial roles as packet switches, forwarding data packets along their journey. Routers typically operate within the network core, connecting multiple networks, while link-layer switches manage data flow within a single network, ensuring that data reaches its destination efficiently.
Understanding these protocols is essential for anyone looking to grasp how the internet functions or troubleshoot network issues. This blog will delve into the OSI model, TCP/IP model, and UDP, exploring their roles and answering key questions about their functionalities.
The OSI Model
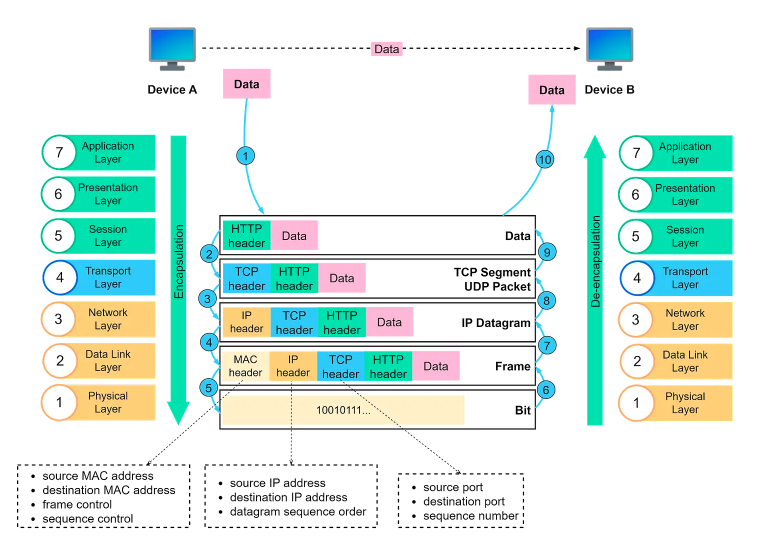
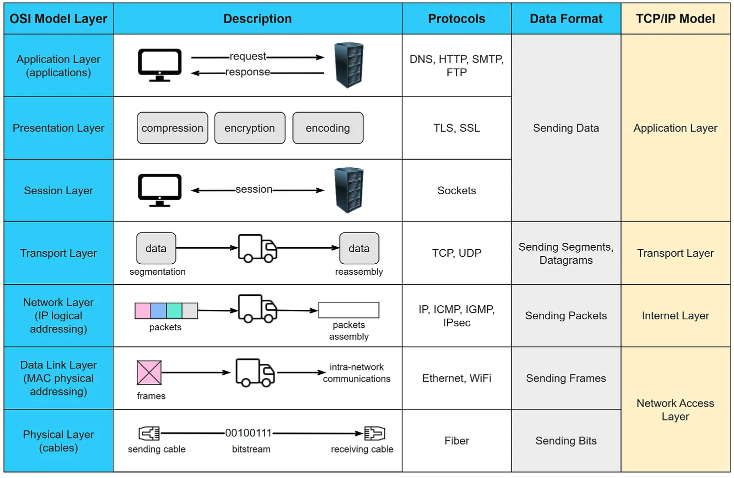
The Open Systems Interconnection (OSI) model is a conceptual framework that standardizes the functions of a telecommunication or computing system, regardless of its underlying structure or technology. It consists of seven layers, each with a distinct role in data communication.
1. Application Layer
- How It Works: This is the layer closest to end-users. It provides network services to applications, such as web browsers or email clients. Protocols at this layer include HTTP (Hypertext Transfer Protocol), SMTP (Simple Mail Transfer Protocol), and FTP (File Transfer Protocol).
- Why It’s Necessary: It allows applications to communicate over the network without needing to understand the specifics of data transmission. For example, when you access a website, HTTP protocols handle the requests and responses between your browser and the server.
2. Presentation Layer
- How It Works: This layer is responsible for data translation, encryption, and compression. It ensures that data from the application layer is presented in a format understandable by the receiving application.
- Why It’s Necessary: It translates data between the formats required by the application and the format used for transmission, providing security through encryption (e.g., HTTPS) and reducing the amount of data sent over the network.
3. Session Layer
- How It Works: The session layer establishes, manages, and terminates connections between applications. It ensures that sessions are properly opened and closed and can manage data transfer checkpoints.
- Why It’s Necessary: It maintains the state of communication sessions, ensuring that data exchanges are properly synchronized and can be resumed or restarted if necessary.
4. Transport Layer
- How It Works: This layer is responsible for end-to-end communication and data integrity. It breaks data into segments, adds headers with sequencing information, and ensures reliable delivery through flow control. Key protocols here include TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
- Why It’s Necessary: It ensures data is transmitted accurately and in the correct order. TCP provides reliability with error checking and correction, while UDP offers faster data transfer with minimal overhead.
5. Network Layer
- How It Works: The network layer handles routing and forwarding of packets across different networks. It breaks down data into packets, adds IP addresses, and determines the best path for data to travel.
- Why It’s Necessary: It enables data to be sent across multiple networks and reaches the correct destination by determining the optimal route using IP addresses.
6. Data Link Layer
- How It Works: This layer is responsible for data transfer within a single network segment. It encapsulates packets into frames and uses MAC addresses to identify devices on the same network.
- Why It’s Necessary: It ensures that data is correctly framed and transferred between devices on the same network, handling error detection and correction at the local level.
7. Physical Layer
- How It Works: The physical layer deals with the actual transmission of raw bitstreams over physical media such as cables, switches, and network interfaces.
- Why It’s Necessary: It facilitates the physical connection between devices and the transmission of data as electrical, optical, or radio signals.
The TCP/IP Model
The TCP/IP model, used practically in most networks today, simplifies the OSI model into four layers:
1. Application Layer
- Function: Combines the OSI model’s Application, Presentation, and Session layers. It includes protocols such as HTTP, FTP, and DNS.
2. Transport Layer
- Function: Includes TCP and UDP. TCP provides reliable, connection-oriented communication, while UDP offers a connectionless, faster alternative with less overhead.
3. Internet Layer
- Function: Corresponds to the OSI Network layer. It handles IP addressing and routing, ensuring that packets travel across networks and reach their destination.
4. Network Interface Layer
- Function: Combines the OSI Data Link and Physical layers. It manages data transfer over physical network links.
UDP and Its Characteristics
UDP (User Datagram Protocol) is a transport layer protocol known for its simplicity and speed. Unlike TCP, UDP does not establish a connection before sending data and does not guarantee delivery, order, or error correction.
- Why UDP Is Considered Unreliable: It does not provide mechanisms for ensuring that packets are delivered or received in order. There are no acknowledgments or retransmissions, which makes UDP faster but less reliable compared to TCP. It is often used in applications where speed is crucial and occasional data loss is acceptable, such as streaming video or online gaming.
Answering Key Questions
a. What happens when we type a URL in a web browser?
The browser sends an HTTP request to the server associated with the URL. This request travels through various layers of the OSI or TCP/IP model, eventually reaching the server, which processes the request and sends back an HTTP response.
b. What is the TCP 3-way handshake?
It is a process used to establish a TCP connection between a client and server. It involves three steps:
- SYN: The client sends a synchronization request.
- SYN-ACK: The server acknowledges the request and sends a synchronization acknowledgment.
- ACK: The client acknowledges the server’s response, establishing the connection.
c. What is TCP time_wait?
It is a state in TCP where a connection is closed but still remains in a waiting period to ensure all data has been transmitted and acknowledged. This prevents old packets from being mistakenly interpreted as part of a new connection.
d. What are HTTP 1/2/3?
- HTTP/1.1: The original version of HTTP that introduced persistent connections.
- HTTP/2: Improved performance with features like multiplexing and header compression.
- HTTP/3: Uses QUIC (Quick UDP Internet Connections), which operates over UDP, offering reduced latency and improved performance compared to its predecessors.
e. Why does HTTP/3 use UDP?
HTTP/3 uses UDP to reduce latency and improve performance. QUIC, the protocol underlying HTTP/3, allows for faster connection establishment and improved handling of packet loss compared to TCP.
f. How does HTTPS work?
HTTPS (Hypertext Transfer Protocol Secure) uses TLS (Transport Layer Security) to encrypt data transmitted between a client and server. It ensures that data is secure and private, protecting against eavesdropping and tampering.
Understanding these concepts is essential for anyone involved in network design, troubleshooting, or development. By grasping the roles of different network protocols and models, you can better navigate and optimize the complex world of network communications.